Written by Debbie Karcher
Cybersecurity is probably a high priority in your district but having the resources in place to effectively manage these threats is difficult. The awareness campaigns, policies, and tools that are currently in place add to a safer environment. However, unless the district’s efforts are documented to demonstrate a degree of organizational cybersecurity readiness the district could be held negligent should a threat occur. To demonstrate that a district has a cybersecurity plan in place consider the Three C’s of Cybersecurity; Chief Support, Create a Cybersecurity Strategy, and Change the Culture.
Chief Support
This can be immediate and doesn’t have a cost. Cybersecurity prevention must begin with the Superintendent and his leadership team. This must be a high priority and leadership needs to be an example and the change agent. Cybersecurity has long been an Information Technology (IT) function because in the past threat prevention aimed at stopping SPAM, viruses, and and inappropriate content. Today the threats have multiple entry points making all employees and connections a vulnerability. There are an innumerable number of attacks that can threaten data, finances, and bring down entire computer systems. The newest and most growing threat is cryptojacking, or malicious cryptomining, that can slow down your computers, increase your power bills and put your security at risk. Making matters worse, in 2018 it took companies an average of 191 days to identify a data breach with 92% of malware arriving through email. Because of the continuous and changing threats, cybersecurity must be addressed throughout the organization with the Superintendent leading the charge.
Create a Cybersecurity Strategy
While creating a comprehensive strategy a near-term solution should be implemented. The following can be applied to small, midsize or large districts. Districts have many tools and activities in place to prevent a cybersecurity attack. These would include policies, procedures, controls, threat prevention software/hardware, password management, communications, and cybersecurity insurance. An inventory of every solution should be documented and reviewed. This first inventory should be quick and require very little in personnel resources. The following is an example of what should be included in a cybersecurity inventory.
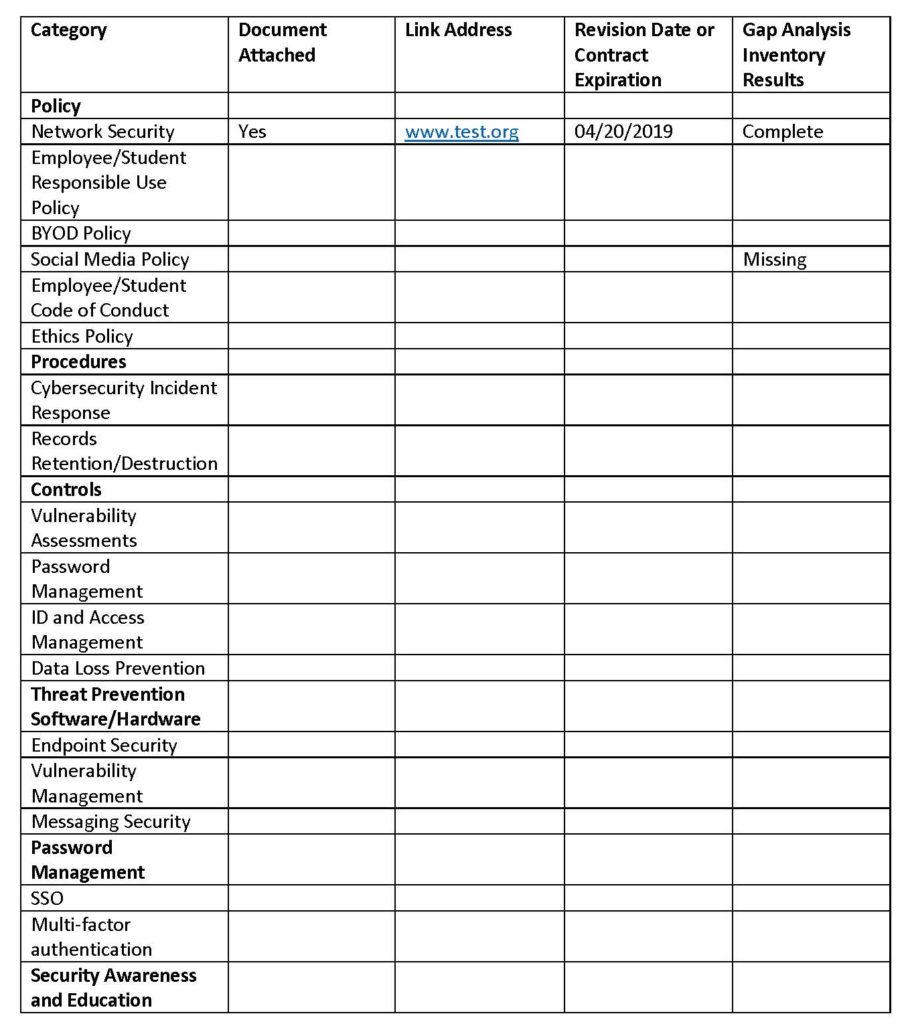
Once the inventory is complete the district can now move into a long-term cybersecurity strategy. The district should select industry best practices (COSN) or industry standards such as the NIST or ISO 2700 and perform a gap analysis. This decision should be made with your auditors, so all auditable elements can be identified and communicated. The inventory can be extended to add the gap analysis results and add any new requirements. The district will need to prioritize the missing requirements based on risk of exposure and costs. Some costs be untenable for many districts, but mitigation alternatives should be identified. The plan can be executed over time, but the district should be able to prove due diligence in implementing the plan.
Change the Culture
This is hard for districts. The business applications, such as finance, human capital, and payroll were usually well protected using passwords, VPNs and a limited number of users. As technology reached all employees and students the districts also became victims of hacking, malware, key loggers, ransomware, and identity theft. Additionally, every classroom could potentially have 20-30 students who are trying to find a way to break into the electronic gradebook or pay for a Denial of Service (DoS) attack so that computer-based high-stake testing is interrupted.
Multiple training sessions, reminders, and security awareness activities need to occur so that everyone understands the importance of their data. Employees, students, and parents need to understand that their personal and district information are as valuable as their banking applications. They must go to any length to protect this. But this can take, for large districts, anywhere from 3-5 years. Some suggestions for a quick result and low-cost solutions include raising cybersecurity awareness among all stakeholders. Districts can start by holding activities during Cybersecurity Awareness Month where emphasis is placed on good cyber security habits and heightened awareness. Examples include, students leaving notes for those students and teachers who leave their computers unlocked and security personnel could send mock phishing emails.
An example of a solution that will take time, but systems may be available, is to change the district’s communications model. At the beginning of this article it was mentioned that 92% of malware comes through email. Because of this threat changing how districts communicate should be a priority when creating their cybersecurity plan. Instead of email, districts need to use private social media sites and content management systems. Texting and instant messaging is also an alternative. As this will be a huge shift for everyone the plan should include training and support.
Cybersecurity prevention when led by your organization leadership followed by low costs activities that can begin to reduce the risk of a cyber-attack is a start. This should be followed by development of a comprehensive cybersecurity plan that includes incident response plans that undergo constant review and revision.